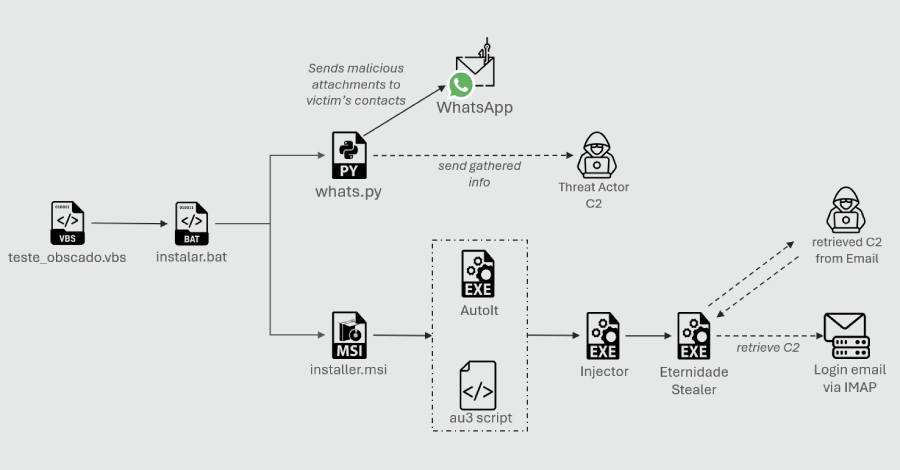
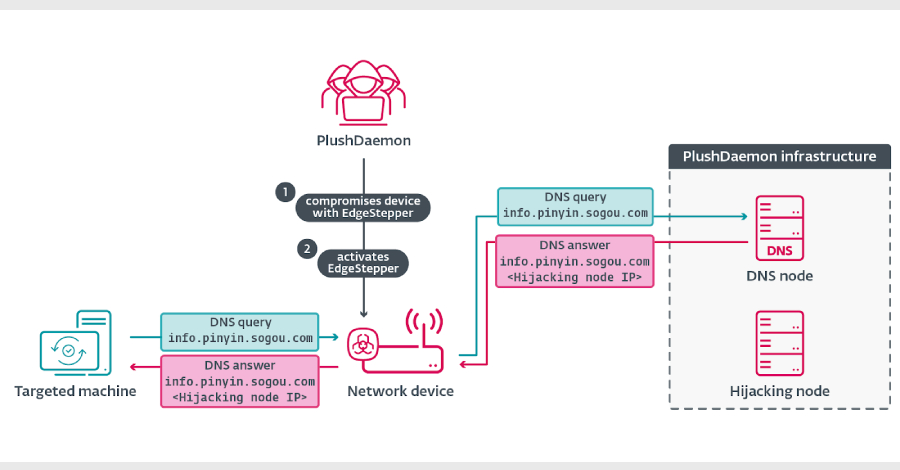
A recently disclosed security flaw impacting 7-Zip has come under active exploitation in the wild, according to an advisory issued by the U.K. NHS England Digital on Tuesday.
The vulnerability in question is CVE-2025-11001 (CVSS score: 7.0), which allows remote attackers to execute arbitrary code. It has been addressed in 7-Zip version 25.00 released in July 2025.
“The specific flaw exists