Cyber News & Articles

Why SOC Burnout Can Be Avoided: Practical Steps
Behind every alert is an analyst; tired eyes scanning dashboards, long nights spent on false positives, and the constant fear of missing something big. It’s no surprise that many SOCs face burnout before they face their next breach. But this doesn’t have to be the norm. The path out isn’t through working harder, but through working smarter, together.
Here are three practical steps every SOC can

CISA Adds Gladinet and CWP Flaws to KEV Catalog Amid Active Exploitation Evidence
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added two security flaws impacting Gladinet and Control Web Panel (CWP) to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild.
The vulnerabilities in question are listed below –
CVE-2025-11371 (CVSS score: 7.5) – A vulnerability in files or directories accessible to

A Cybercrime Merger Like No Other — Scattered Spider, LAPSUS$, and ShinyHunters Join Forces
The nascent collective that combines three prominent cybercrime groups, Scattered Spider, LAPSUS$, and ShinyHunters, has created no less than 16 Telegram channels since August 8, 2025.
“Since its debut, the group’s Telegram channels have been removed and recreated at least 16 times under varying iterations of the original name – a recurring cycle reflecting platform moderation and the operators’

Europol and Eurojust Dismantle €600 Million Crypto Fraud Network in Global Sweep
Nine people have been arrested in connection with a coordinated law enforcement operation that targeted a cryptocurrency money laundering network that defrauded victims of €600 million (~$688 million).
According to a statement released by Eurojust today, the action took place between October 27 and 29 across Cyprus, Spain, and Germany, with the suspects arrested on charges of involvement in
The AI Fix #75: Claude’s existential battery crisis, and why ChatGPT is a terrible therapist
In episode 75 of The AI Fix, a Claude-powered robot gets so anxious about its dying battery that it composes a Broadway musical about stress and announces it’s “achieved consciousness and chosen chaos.”
Also: an 18-month psychological study reveals five reasons why ChatGPT is a dangerously bad therapist, Elon Musk’s million-robot army, a politician loses a debate with a dreadful AI deepfake, a tiny robot walks off with a 1.5-ton car, and we discover that the 1X NEO home help robot really does have a person inside it.
All this and much more is discussed in the latest edition of “The AI Fix” podcast by Graham Cluley and Mark Stockley.
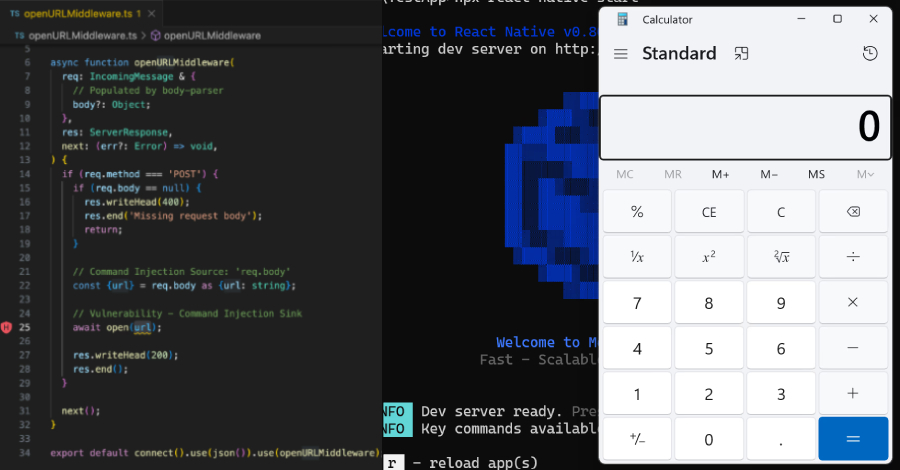
Critical React Native CLI Flaw Exposed Millions of Developers to Remote Attacks
Details have emerged about a now-patched critical security flaw in the popular “@react-native-community/cli” npm package that could be potentially exploited to run malicious operating system (OS) commands under certain conditions.
“The vulnerability allows remote unauthenticated attackers to easily trigger arbitrary OS command execution on the machine running react-native-community/cli’s

Microsoft Teams Bugs Let Attackers Impersonate Colleagues and Edit Messages Unnoticed
Cybersecurity researchers have disclosed details of four security flaws in Microsoft Teams that could have exposed users to serious impersonation and social engineering attacks.
The vulnerabilities “allowed attackers to manipulate conversations, impersonate colleagues, and exploit notifications,” Check Point said in a report shared with The Hacker News.
Following responsible disclosure in March

Ransomware Defense Using the Wazuh Open Source Platform
Ransomware is malicious software designed to block access to a computer system or encrypt data until a ransom is paid. This cyberattack is one of the most prevalent and damaging threats in the digital landscape, affecting individuals, businesses, and critical infrastructure worldwide.
A ransomware attack typically begins when the malware infiltrates a system through various vectors such as

Operation SkyCloak Deploys Tor-Enabled OpenSSH Backdoor Targeting Defense Sectors
Threat actors are leveraging weaponized attachments distributed via phishing emails to deliver malware likely targeting the defense sector in Russia and Belarus.
According to multiple reports from Cyble and Seqrite Labs, the campaign is designed to deploy a persistent backdoor on compromised hosts that uses OpenSSH in conjunction with a customized Tor hidden service that employs obfs4 for

Google’s AI ‘Big Sleep’ Finds 5 New Vulnerabilities in Apple’s Safari WebKit
Google’s artificial intelligence (AI)-powered cybersecurity agent called Big Sleep has been credited by Apple for discovering as many as five different security flaws in the WebKit component used in its Safari web browser that, if successfully exploited, could result in a browser crash or memory corruption.
The list of vulnerabilities is as follows –
CVE-2025-43429 – A buffer overflow
