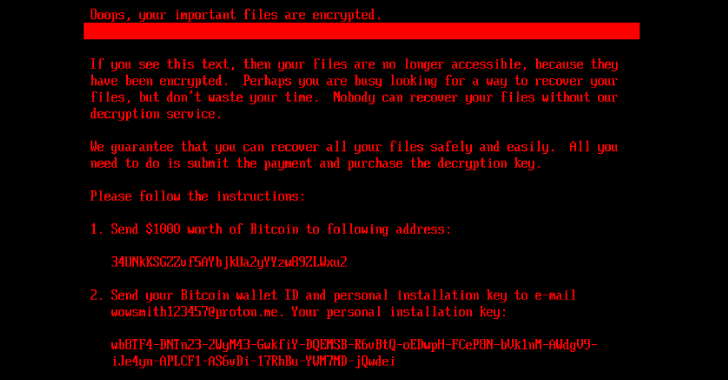
Cybersecurity researchers have discovered a new ransomware strain dubbed HybridPetya that resembles the notorious Petya/NotPetya malware, while also incorporating the ability to bypass the Secure Boot mechanism in Unified Extensible Firmware Interface (UEFI) systems using a now-patched vulnerability disclosed earlier this year.
Slovakian cybersecurity company ESET said the samples were uploaded