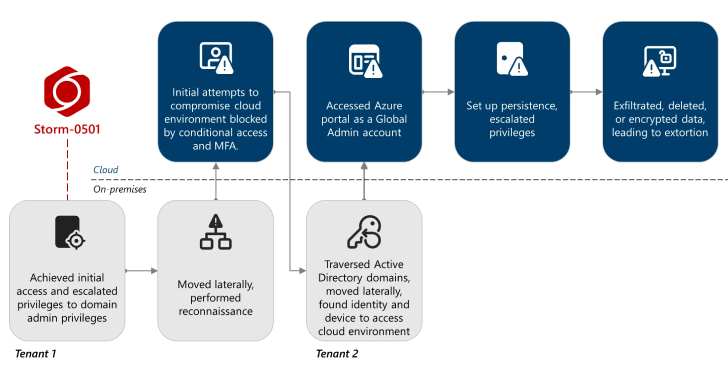
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) announced a fresh round of sanctions against two individuals and two entities for their role in the North Korean remote information technology (IT) worker scheme to generate illicit revenue for the regime’s weapons of mass destruction and ballistic missile programs.
“The North Korean regime continues to target American