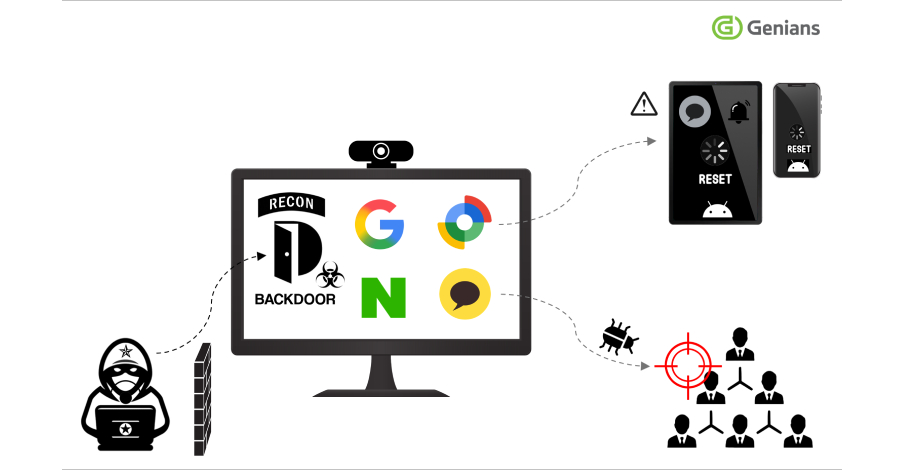
Google’s Mandiant Threat Defense on Monday said it discovered n-day exploitation of a now-patched security flaw in Gladinet’s Triofox file-sharing and remote access platform.
The critical vulnerability, tracked as CVE-2025-12480 (CVSS score: 9.1), allows an attacker to bypass authentication and access the configuration pages, resulting in the upload and execution of arbitrary payloads.
The