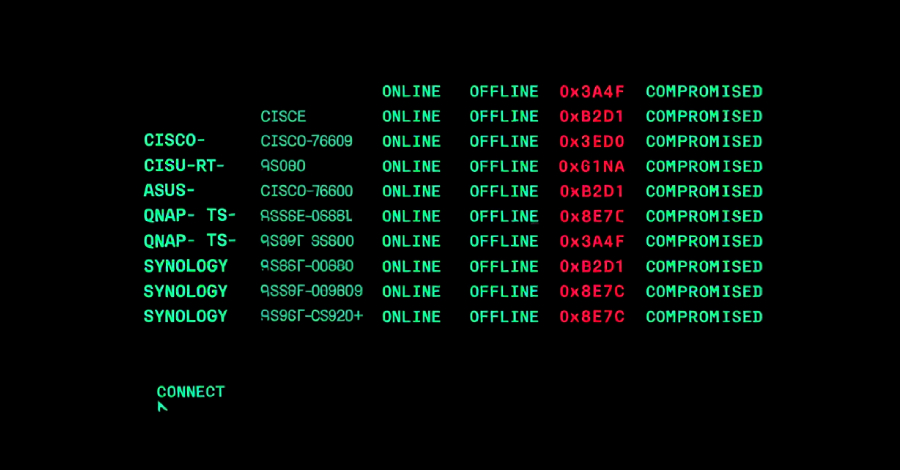
Cybersecurity researchers have shed light on the inner workings of a botnet malware called PolarEdge.
PolarEdge was first documented by Sekoia in February 2025, attributing it to a campaign targeting routers from Cisco, ASUS, QNAP, and Synology with the goal of corralling them into a network for an as-yet-undetermined purpose.
The TLS-based ELF implant, at its core, is designed to monitor