Cyber News & Articles

South African man imprisoned after ransom demand against his former employer
Lucky Erasmus and a company insider installed software without authorisation on Ecentric’s systems which granted them remote access, enabling them to steal sensitive data and make unauthorised changes to senior managers’ passwords.
Read more in my article on the Hot for Security blog.

Apple Zero-Click Flaw in Messages Exploited to Spy on Journalists Using Paragon Spyware
Apple has disclosed that a now-patched security flaw present in its Messages app was actively exploited in the wild to target civil society members in sophisticated cyber attacks.
The vulnerability, tracked as CVE-2025-43200, was addressed on February 10, 2025, as part of iOS 18.3.1, iPadOS 18.3.1, iPadOS 17.7.5, macOS Sequoia 15.3.1, macOS Sonoma 14.7.4, macOS Ventura 13.7.4, watchOS 11.3.1,
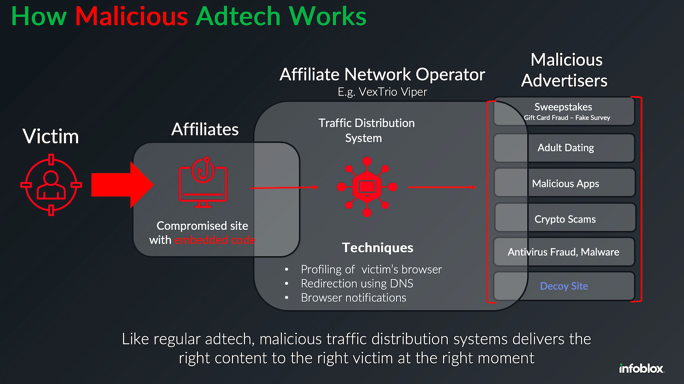
Inside a Dark Adtech Empire Fed by Fake CAPTCHAs
Late last year, security researchers made a startling discovery: Kremlin-backed disinformation campaigns were bypassing moderation on social media platforms by leveraging the same malicious advertising technology that powers a sprawling ecosystem of online hucksters and website hackers. A new report on the fallout from that investigation finds this dark ad tech industry is far more resilient and incestuous than previously known.
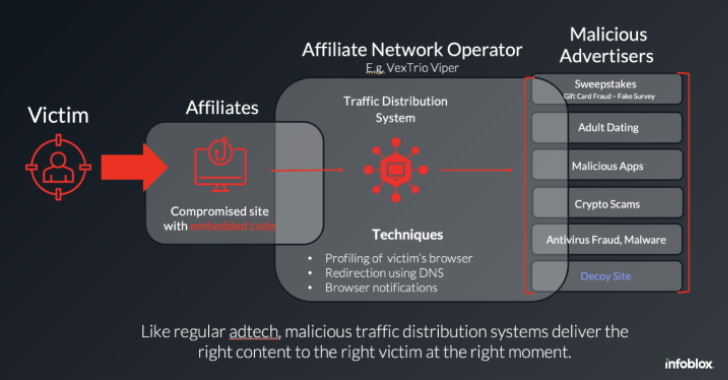
WordPress Sites Turned Weapon: How VexTrio and Affiliates Run a Global Scam Network
The threat actors behind the VexTrio Viper Traffic Distribution Service (TDS) have been linked to other TDS services like Help TDS and Disposable TDS, indicating that the sophisticated cybercriminal operation is a sprawling enterprise of its own that’s designed to distribute malicious content.
“VexTrio is a group of malicious adtech companies that distribute scams and harmful software via

Sweden says it is under cyber attack
Swedish Prime Minister Ulf Kristersson says his country is under attack, after days of hard-hitting DDoS attacks against SVT Sweden’s public TV broadcaster, government websites, and other key organisations.
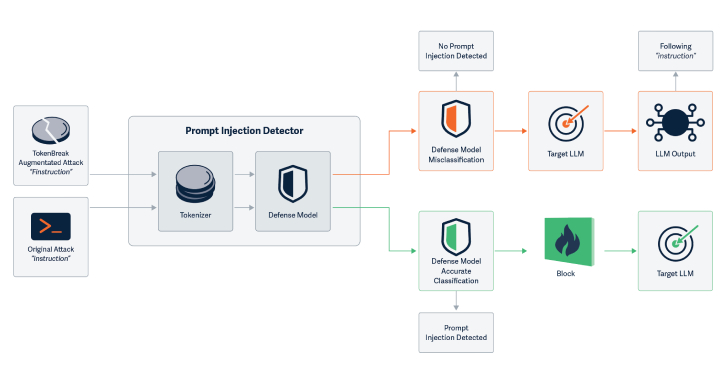
New TokenBreak Attack Bypasses AI Moderation with Single-Character Text Changes
Cybersecurity researchers have discovered a novel attack technique called TokenBreak that can be used to bypass a large language model’s (LLM) safety and content moderation guardrails with just a single character change.
“The TokenBreak attack targets a text classification model’s tokenization strategy to induce false negatives, leaving end targets vulnerable to attacks that the implemented

AI Agents Run on Secret Accounts — Learn How to Secure Them in This Webinar
AI is changing everything — from how we code, to how we sell, to how we secure. But while most conversations focus on what AI can do, this one focuses on what AI can break — if you’re not paying attention.
Behind every AI agent, chatbot, or automation script lies a growing number of non-human identities — API keys, service accounts, OAuth tokens — silently operating in the background.
And here’s
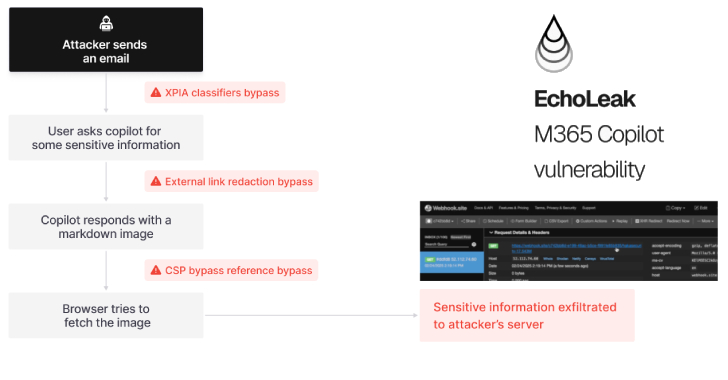
Zero-Click AI Vulnerability Exposes Microsoft 365 Copilot Data Without User Interaction
A novel attack technique named EchoLeak has been characterized as a “zero-click” artificial intelligence (AI) vulnerability that allows bad actors to exfiltrate sensitive data from Microsoft 365 Copilot’s context sans any user interaction.
The critical-rated vulnerability has been assigned the CVE identifier CVE-2025-32711 (CVSS score: 9.3). It requires no customer action and has been already

Non-Human Identities: How to Address the Expanding Security Risk
Human identities management and control is pretty well done with its set of dedicated tools, frameworks, and best practices. This is a very different world when it comes to Non-human identities also referred to as machine identities. GitGuardian’s end-to-end NHI security platform is here to close the gap.
Enterprises are Losing Track of Their Machine Identities
Machine identities–service

Malware attack disguises itself as DeepSeek installer
Cybercriminals are exploiting the growing interest in open source AI models by disguising malware as a legitimate installer for DeepSeek.
